Hey there! It’s been a little while since I’ve checked-in, but I’m back, and I have a brand new article!
Hopefully, you’ve read through my previous articles on blogging … and maybe checked out my first YouTube video review (it’s for a lawn mower I’m kind of in love with). If you haven’t looked yet, the links are right here:
 |
 |
 |
 |
 |
Something I’ve tried to weave into my previous blogging posts is a topic that may not be front-of-mind; however, it is an absolute must if you’re serious about writing: How to secure your WordPress site.
I have some great tips for you, including some simple plug-ins you might want to think about — all designed to keep the bad stuff out, so you can worry about something else far more important … like content.
There are, basically, three topics I’m going to cover: keeping the bad guys out, performing your updates, and responding when it happens.
Guard Your Walls
Here’s a scary thing. You can go to just about ANY WordPress site, and after the domain add “/wp-admin” and get to their login page. Try it. Pick a website that you know runs WordPress, type in their domain, and add the suffix: www.domain.com/wp-admin (but please don’t go any further).
Now ask yourself how many nefarious strangers visit your back-end login page in a day. Hopefully none … but who knows?
The bad guys want access to your site, typically, for one of four reasons:
- They want to install a drive-by-download on your page that will automatically download a malware payload to your audience, potentially turning their machines into malware zombies for later attacks,
- They want to use your site and your audience to distribute SPAM emails by the thousands,
- They want to post articles to promote their agenda, or
- They’re targeting you and want to sabotage what you’ve created.
 It helps if you think about your site security like your house: If someone is bound and determined to get inside, they’ll break a window and come in. If someone is simply trolling for an easy mark, having lights on, installing a security system, owning a guard/alarm dog, adding good door locks, or digging a moat are all ways to deter someone looking to pick the low hanging fruit.
It helps if you think about your site security like your house: If someone is bound and determined to get inside, they’ll break a window and come in. If someone is simply trolling for an easy mark, having lights on, installing a security system, owning a guard/alarm dog, adding good door locks, or digging a moat are all ways to deter someone looking to pick the low hanging fruit.
If you try to make your site unattractive to those looking for the easy mark, you’re 90% there.
The bad news first: if someone is specifically targeting your site, intent on bringing-down your blog specifically, and they know what they’re doing (and have a major grudge), there’s very little you can do to stop them; HOWEVER, of all the attacks that occur, this type of attack is by far the least popular since it can be so incredibly time consuming and leave some easy-to-follow tracks afterward.
The good news: for the first three bullets above, there’s a lot you can do to keep the bad guys away.
- Limit the Users you have and MAKE CERTAIN they have strong passwords. When I speak on website security, this is always the first point I make. The easiest thing you can do to prevent an attack is make your password difficult to guess. There are utilities out there (for free) that will guess passwords in seconds — and they’re good at it. The first time I saw a password cracking tool, I was shocked at how efficient it was. So please take this advice when crafting your password:
- Use UPPERCASE LETTERS, use lowercase letters, use numbers, and use the characters above the number keys.
- Do not use a name, a city, a dictionary word, a month, a car, or something else that’s easily guessed.
- Not a password tip, but if you have a user named ADMIN … kill it. Change the account name. Disable it and create a new admin using another name. Change the existing name from ADMIN to anything else. Likewise with GUEST.
- Make certain your computer’s antivirus is running and is current. If you don’t have one, stop what you’re doing and install a free one ASAP (Avast, AVG, or Microsoft Security Essentials). This is an absolute must. If your computer has some cooties, you could be automatically sending every single keystroke to a bad guy, which not only tells them how to log onto your blog, but also how to access your bank account, amazon account, Facebook account … basically anywhere you enter a username and password.
- Open your antivirus and check to see when it last updated. It should be today or yesterday. If it hasn’t updated in the last week, install another one because it should have.
- Run a scan. Frequently, antivirus software is scheduled to run in the early morning; however, many of us put our computers to sleep at night, so your machine is off when your AV attempts to run. Change the schedule so it runs during the day, when you know you’ll have it on.
- Consider some plugins. If you search for “WordPress hardening plugin”, you’re likely to find a plethora of tools to help harden your site. Some are helpful. Some will screw you. So please do the research and read the reviews before installing anything.
- A captcha at the login screen can be helpful. Maybe. There are blackhat tools out there that breeze through a captcha like it doesn’t even exist, but it can add a layer of security that will likely stop of a few attempts.
- Set secure file permissions. Some plugins will offer this, and it’s a good thing.
- Secure wp-config.php. Anymore, this is something that WordPress mandates at install, but it’s good to check.
- Install a logging plug-in. There’s a very basic plug-in that does nothing more than log the IP, Date, Time, and User ID each time someone logs into your Admin page — just make sure you review it.
Patches. You NEED your stinkin’ patches.
Your site has vulnerabilities. Every site does regardless of CMS.
That’s a fact. There are hundreds of thousands of lines of code that allow your glorious site to do what it does all day everyday. You really have to stand back and marvel at how much time and effort went into giving you your web site (probably for free).
But the code was written by humans, and humans are fallible.
Thankfully, there are brilliant programmers out there, right now, working to identify and fix those weak spots. Eventually, once they’ve found the hole, written the code to fix it, tested it, bundled it, and distributed it, YOU will have the opportunity to apply it in the form of an update.
Know this: by the time a patch gets to you, it’ll be weeks after a vulnerability was discovered, so it’s pretty crucial that you apply the patch as soon as you’re able.
WordPress has three main categories for patches: The CMS (WordPress itself), plug-ins, and themes. It’s important that you patch all categories, including themes and plug-ins you have installed but deactivated.
Here are my tips:
- Update as often as you’re able, but select the right time. We do ours weekly, right after the site backup successfully completes. This is by design in case we apply an update to a plugin that hoses the site, we can always go back to a backup and restore to where we were before applying the broken fix. Thankfully, we’ve never needed to, but I’m a little more comfortable applying patches knowing I have a back to fall back on if need be.
- In the UPDATE section of WordPress, look at the information it’s telling you. Take a note of the version number. Understand if you’re about to apply a big change or not — check out the graphic below.
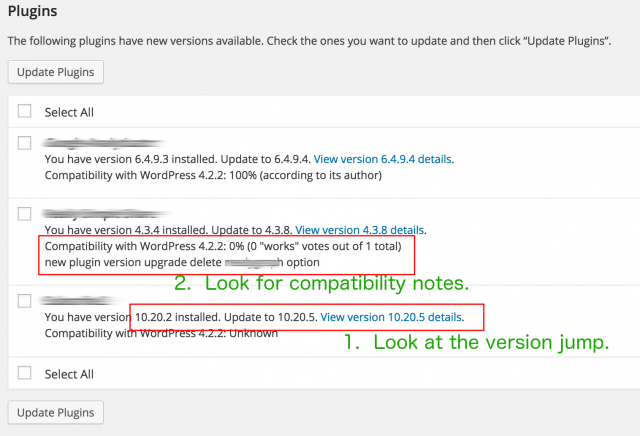
- If we look at the version number that’s highlighted, the installed version in 10.20.2, but the current version is 10.20.5.
- In versioning the first number (10.) indicates a major change, typically a significant interface adjustment.
- The second number (20.) contains some big changes, but probably not something that dramatically impacts functionality.
- The third number (5) usually means it’s a smaller update, containing bug fixes.
- Please note: This isn’t math class, so 1.1.9 is less than 1.1.10. I’m sorry if that annoys you … I didn’t come up with it.
- Look at the compatibility notes — but take it with a grain of salt. The notes here aren’t gospel (even if the author says it’s 100% compatible), but it’s still a good thing to be aware of.
- If we look at the version number that’s highlighted, the installed version in 10.20.2, but the current version is 10.20.5.
- You can be defensive with plug-ins by limiting the number you have installed (active and inactive). Although they can be a lot of fun, ask yourself if you really need all the plug-ins you have installed.
How To React
If you’ve discovered that your website has a breach, first and foremost: don’t freak out. You might get a black-eye, and you might need to reach out to a few vendors to ask forgiveness, but your brand will recover. Your vendors will understand. Your readers will understand. You will recover.
WordPress offers a TON of great advice on this page.
Basically, you start be trying to clean the cooties — on your computer and your site. This may mean restoring from a backup, so please make sure you have a good one.
Next, if you can log in, you need to change the password for every user with access.
Then you secure your page by going through a lot of the steps I’ve mentioned above.
For tips, lean on the WordPress community. There are millions of installations of WP out there, and there’s a tremendous collection of smart users willing to help. Check out their Hacked or their Malware forums for assistance from your peers.
That’s about it.
Obviously, there are so many facets to web site security, I couldn’t begin to get into it all, but hopefully, this offers a little assistance to help ward off any drive-by attacks and prevent you from becoming the vulnerable, low hanging fruit.
I have quite a bit of experience in network security, and I’d be willing to try and answer any questions you might have below. So please ask away, and maybe your question will help someone else.
Thanks for letting me visit again.
And please check out my other posts mentioned above.

Thanks so much for writing this series!! It’s not only helpful, but entertaining.
Question: Is the content in my blog my intellectual property, or do I need to copyright?
Great question. Here’s an article that discusses that very issue: https://www.legalzoom.com/articles/blogging-and-intellectual-property-law